Welcome to our brand-new series on Microsoft 365 updates! Each month, we’ll bring you the latest developments across Microsoft’s ecosystem. Over the past 30 days, Microsoft has rolled out an impressive 195 updates to M365. This month’s picks, selected by our Chief Technology Officer, Viam Mercer, highlight three standout updates—plus a bonus one—that could have a significant impact on your business. Take a look at the details below:
Full Enforcement Mode for Certificate-Based Authentication Changes on Windows DCs - MC959496
Starting in May 2022, certificate-based authentication on Windows domain controllers (DCs) began undergoing a series of changes to enhance security, following a planned timeline of Enablement Phases. On 10 September 2024, Microsoft updated the timeline of security requirements for certificate-based authentication requests on Windows DCs. After you install the Windows security updates released in February 2025, authentication for certificates that do not meet the expected mapping requirements will be denied. This change is known as Full Enforcement mode. However, you can move back to Compatibility mode until September 2025. For full details, see KB5014754.
When will this happen: In February 2025, or later, devices will move to Full Enforcement mode.
How this will affect your organisation: When you install the February 2025 Windows security update, devices that are not already in Full Enforcement mode (StrongCertificateBindingEnforcement registry value is set to 2), will be moved to Full Enforcement mode. If authentication is denied, you will see Event ID 39 (or Event ID 41 for Windows Server 2008 R2 SP1 and Windows Server 2008 SP2). You will have the option to set the registry key value back to 1 (Compatibility mode) at this stage. In the September 2025 Windows update, the StrongCertificateBindingEnforcement registry value will no longer be supported.
What you need to do to prepare: Review the date changes in the “Take action”, “Full Enforcement mode”, and “Registry key information” sections of KB5014754. Take the appropriate action needed to make your devices more secure.
Additional information: For full detailed information, see KB5014754: Certificate-based authentication changes on Windows domain controllers.
Power Platform: Upcoming Enforcement of Tenant Isolation - MC981567
As part of our Secure by Default initiative, the tenant isolation feature will be enabled by default for all Power Platform tenants as the new default behaviour. The enforcement is scheduled to begin the first week of 24 March 2025. This feature applies only to Power Platform policies and is separate from guest access policies and Azure tenant restriction features.
How does this affect me? Tenant isolation only applies to connectors running within a tenant. The default tenant isolation behaviour will block all connection attempts from one tenant to another; inbound (connections to the tenant from external tenants), outbound (connections from the tenant to external tenants), or both (inbound – outbound) will be blocked by Power Platform. Communications within the same tenant will not be affected. In addition, users logging in as guests (guest user access) will remain unaffected.
What do I need to do to prepare? To prevent any disruptions, if our traffic monitoring logs indicate cross-tenant connections involving your tenant, we will proactively set up the necessary policies for you before enforcement. This message is for awareness and no action is required. However, if you prefer to configure policies proactively prior to enforcement, you can do so by following the tenant isolation policy. Additionally, please ensure you identify scenarios currently using cross-tenant connections or anticipate calls to or from other tenants by establishing an allow list of the relevant tenant IDs by following the recommended guidelines.
Updated 24 January 2025: Microsoft has updated the rollout timeline below.
Microsoft Purview Information Protection: Auto-Labelling Policies Will Support "Fingerprint Based SIT" - MC920308
Summary: Auto-labelling policies in Microsoft Purview Information Protection will soon support Fingerprint based SIT. Rollout will start late November 2024 and finish by early February 2025. This update allows admins to automatically label files and emails with Fingerprint based SIT, which will be on by default.
When this will happen: General Availability (Worldwide, GCC, GCC High, DoD): Microsoft will begin rolling out late November 2024 and expect to complete by early February 2025 (previously mid-January).
How this will affect your organisation: Before this rollout, admins are not able to use auto-labelling policies to automatically label files and emails with Fingerprint based SIT. After this rollout, you can configure Fingerprint based SIT using the condition "Content contains sensitive information types." Files that match Fingerprint based SIT will show in simulation.
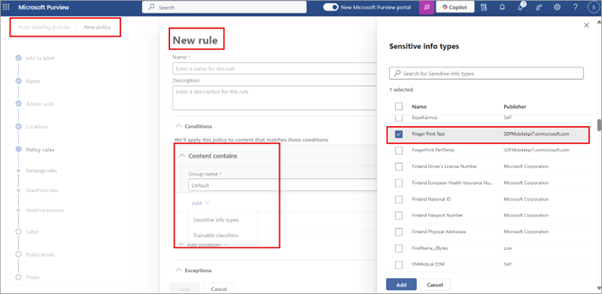
What you need to do to prepare: This rollout will happen automatically by the specified date with no admin action required before the rollout. Review use cases and set up for configuring document fingerprinting.
Learn more:
Microsoft Teams: Brand Impersonation Protection for Teams Chat - MC910976
Summary: Microsoft Teams is introducing a new security feature to alert users of potential brand impersonation in Teams Chat, especially during initial contact from external domains. Rollout begins late October 2024 for Targeted Release and mid-November 2024 for General Availability, completing by mid-February 2025. This feature will be enabled by default with no admin configuration needed.
When this will happen:
- Targeted Release: Microsoft will begin rolling out late October 2024 and expect to complete by late October 2024.
- General Availability (Worldwide): Microsoft will begin rolling out mid-November 2024 and expect to complete by mid-February 2025 (previously mid-January).
How this will affect your organisation:
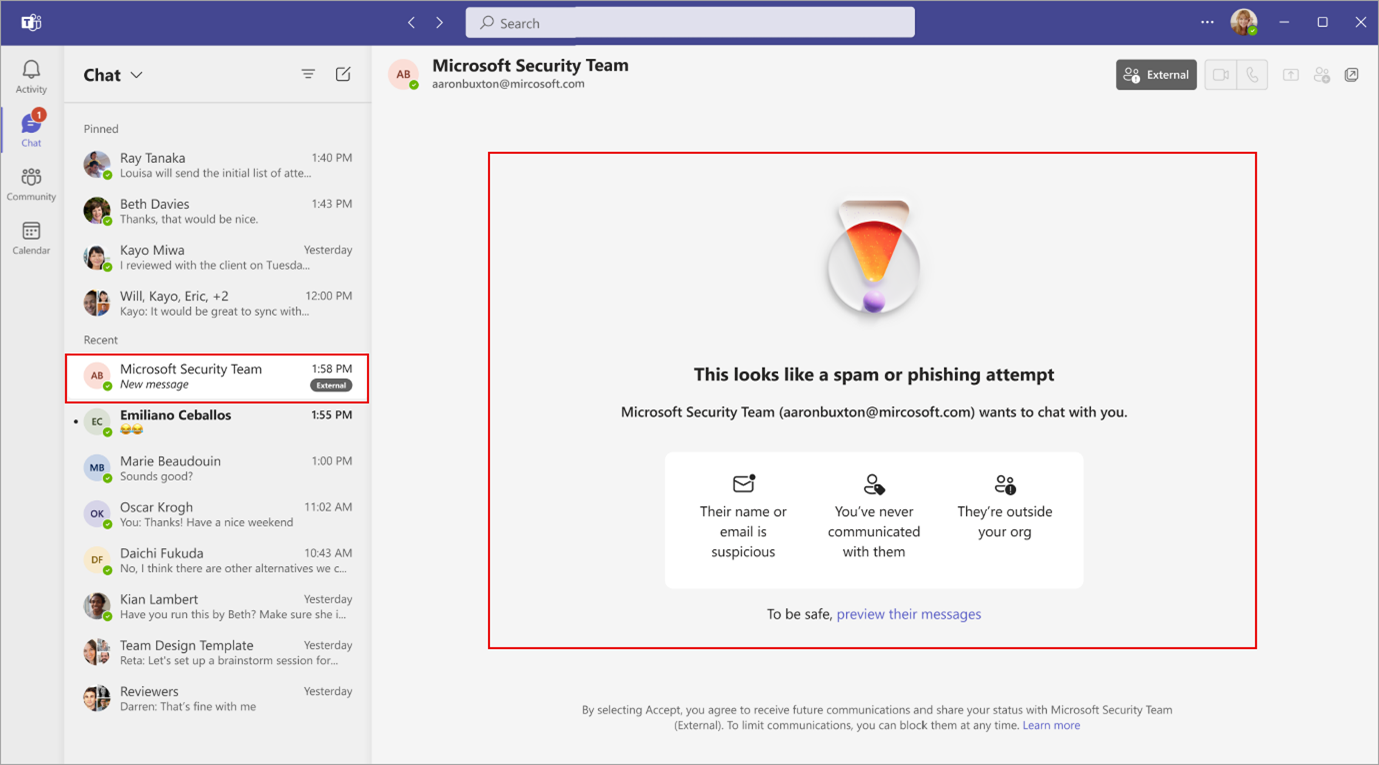
Before this rollout: For organisations that have enabled Teams external access, users can receive messages from any user from an external domain. Teams does not scan the sender for impersonation risks. When a user receives a chat invitation, the user can accept, block, or preview the message. Note: Previewing the message does not put the organisation at risk.
After this rollout: If your organisation enables Teams external access, we will check for potential impersonation activity when your user receives a message from an external sender for the first time. Your users will see a high-risk warning in the Accept/Block flow if we think there is potential impersonation risk, and users must preview the message before they can choose to accept or block. If users choose to accept, we will prompt them again with potential risk before proceeding with acceptance. This security check will be done automatically. No admin configuration is required. Admins can check the audit log for impersonation attempts detected.
When a user selects Preview their messages in the first screen, and then selects Accept, the user is alerted again to the potential for risk in this screen:
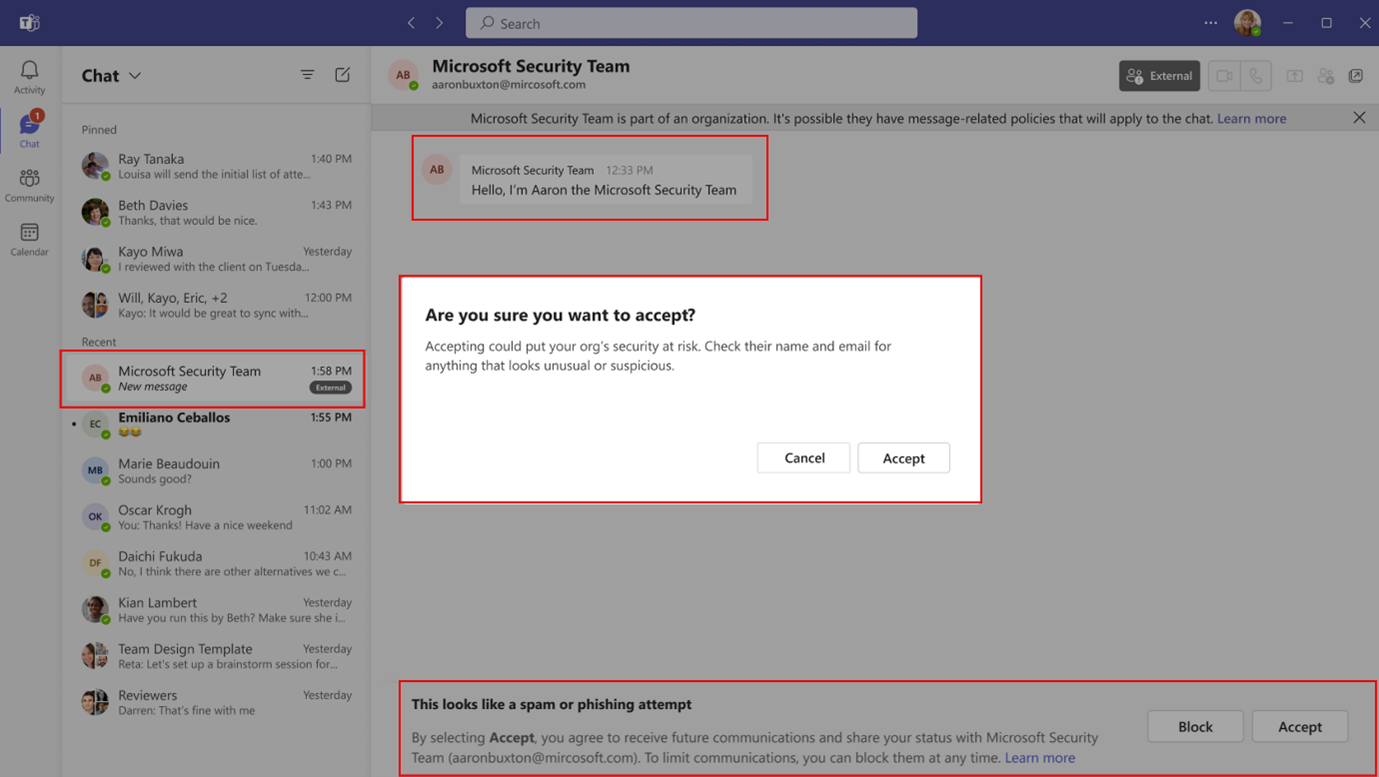
This feature will be on by default.
What you need to do to prepare: This rollout will happen automatically by the specified date with no admin action required before the rollout. You may want to update any relevant documentation. We recommend that you educate your users on what the new high-risk Accept/Block screen means and remind users to proceed with caution.
Do you need support managing your M365 updates?








